Services
Accelerator
Accelerator
Levarne builds software in the cloud. Cloud often refers to infrastructure or the flexible use of computer infrastructure. Levarne, however, uses the software services on the cloud. We call that Cloud Native Applications. During the development of various applications, we named frequently used software blocks and bundled them into one product, the Accelerator. With this bundling we start every new application, both for web and mobile. The Accelerator code is the glue between the customer application and the software services of cloud providers such as Amazon, Microsoft or Google. We ensure that our glue continues to work in the constantly changing services of these providers. If you want to have a new application developed, you prefer to get results as quickly as possible. Levarne uses the blocks to shorten the turnaround time of your application. How does this work? This product can be used as the basis for any new application. Below is a description of the functionalities in our product. Which functionalities are needed depends entirely on the wishes of the customer.
The Accelerator blocks
By naming the building blocks, the complexity immediately becomes clear. Without a strong foundation, future functionalities become unnecessarily expensive, whereby the time to achieve a result also poses a risk.
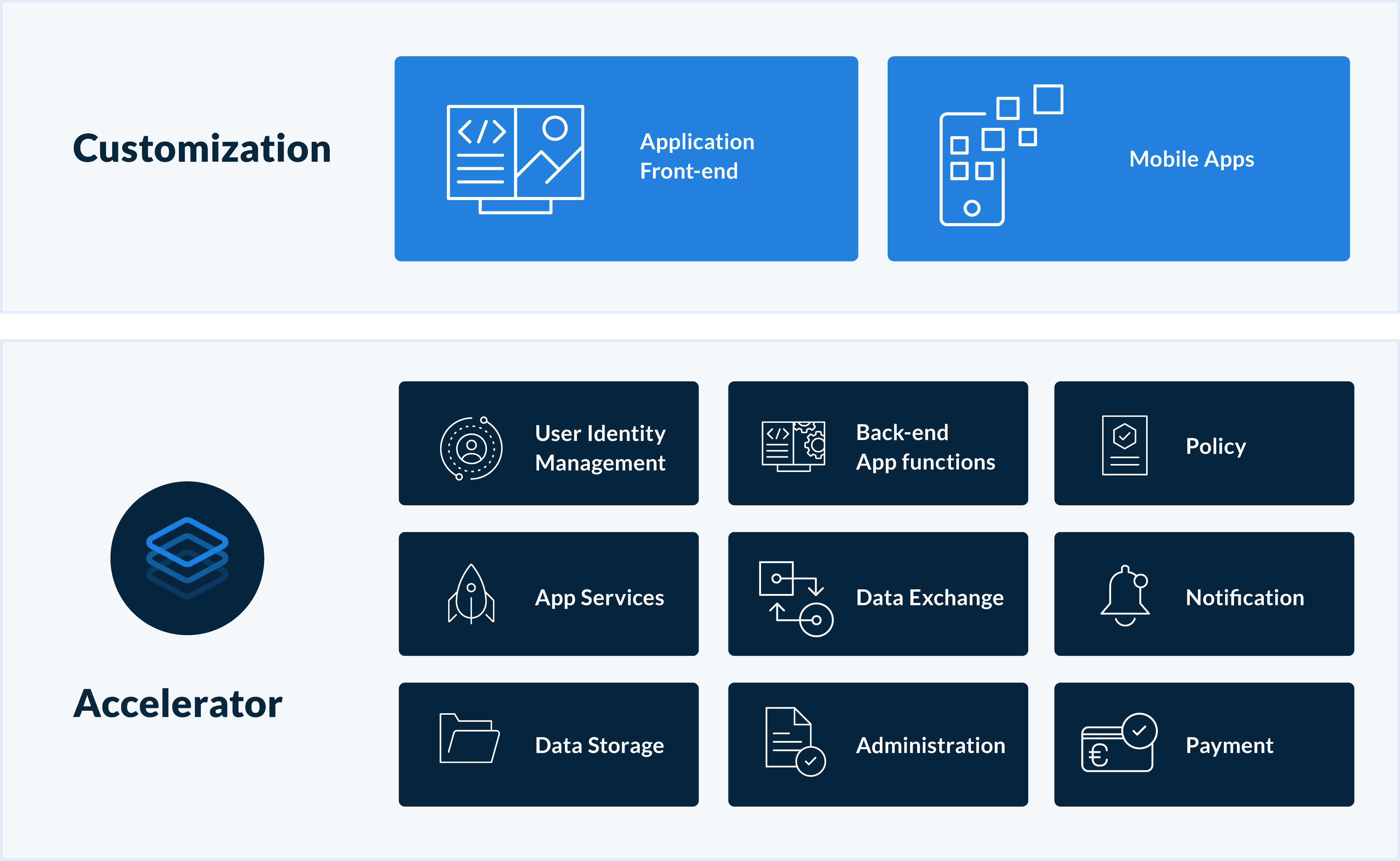
By naming the building blocks, the complexity immediately becomes clear. Without a strong foundation, future functionalities become unnecessarily expensive, whereby the time to achieve a result also poses a risk.

User identity management and Policies
Implementing user management functions to provide users with certain capabilities and manage their roles in the application. Login through social login or email login. Lost password flow, user data disconnected from the user. Log in with QR code, mobile in combination with desktop screens.
The policies apply to all applications that use the pool of users. So all policies also apply to all applications and application functions. By introducing an administration layer, again bound to the same mechanisms, users become simple processes to notify, create or modify.
User identity management and Policies
Implementing user management functions to provide users with certain capabilities and manage their roles in the application. Login through social login or email login. Lost password flow, user data disconnected from the user. Log in with QR code, mobile in combination with desktop screens.
The policies apply to all applications that use the pool of users. So all policies also apply to all applications and application functions. By introducing an administration layer, again bound to the same mechanisms, users become simple processes to notify, create or modify.
Administration
All possible settings, texts, changes to the application flow are in this block. This strongly depends on the choices made in the front-end.
Administration
All possible settings, texts, changes to the application flow are in this block. This strongly depends on the choices made in the front-end.
Notification services
Any application can use signals. Think of email, mobile notification, Chrome notification, everything to demand attention in a user flow using data and events.
Notification services
Any application can use signals. Think of email, mobile notification, Chrome notification, everything to demand attention in a user flow using data and events.
Directory- and App services
Heart of a software product when it comes to roles, rights and different applications that use the same data. An App service example is a matrix of users and application functions or user flows.
Directory- and App services
Heart of a software product when it comes to roles, rights and different applications that use the same data. An App service example is a matrix of users and application functions or user flows.
Security
Our software layers run on infrastructure from public cloud providers. These parties have strongly limited the underlying layers in use and secured them against hacking / abuse. Use of specific network connections between software components and, for example, APIs for different user groups prevents misuse and uncontrollability. If User Identity is entered, policy management, rights and access can be applied immediately without code changes. By applying the policies to application services or back-end functions, security and personal data security becomes a design issue rather than business risk.
Security
Our software layers run on infrastructure from public cloud providers. These parties have strongly limited the underlying layers in use and secured them against hacking / abuse. Use of specific network connections between software components and, for example, APIs for different user groups prevents misuse and uncontrollability. If User Identity is entered, policy management, rights and access can be applied immediately without code changes. By applying the policies to application services or back-end functions, security and personal data security becomes a design issue rather than business risk.
Data Exchange en Data Storage
Every application where data is entered needs some form of data sharing. The input is also not only done by users, external data sources or APIs can also be consulted. The exchange and perhaps also enrichment of data flows is standard functionality. Data Exchange and Data Storage are inextricably linked to integrations with third parties. So simple APIs for integrations with other software packages.
Data Exchange en Data Storage
Every application where data is entered needs some form of data sharing. The input is also not only done by users, external data sources or APIs can also be consulted. The exchange and perhaps also enrichment of data flows is standard functionality. Data Exchange and Data Storage are inextricably linked to integrations with third parties. So simple APIs for integrations with other software packages.
Payment
For applications that require checkout, payments or subscriptions. If the applications have anything to do with commerce, several secure payment options are a must. The most common systems we work with are Mollie, Stripe, PayPal and Apple Pay. However, we can integrate almost any payment method. The variety of payment systems will facilitate transactions for users and increase your application rating. Payment system Integration has two sides: possibility to make payments for the users and the possibility to manage payments for the administrators, in case you integrate a payment system.
Payment
For applications that require checkout, payments or subscriptions. If the applications have anything to do with commerce, several secure payment options are a must. The most common systems we work with are Mollie, Stripe, PayPal and Apple Pay. However, we can integrate almost any payment method. The variety of payment systems will facilitate transactions for users and increase your application rating. Payment system Integration has two sides: possibility to make payments for the users and the possibility to manage payments for the administrators, in case you integrate a payment system.
Architecture and AVG / GDPR
Levarne provides a secure architecture based on The General Data Protection Regulation (EU) 2016/679 (GDPR). "No individual user data is stored near the user's identity." The General Data Protection Regulation (GDPR) has seven design principles:
- Lawfulness, fairness and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality (security)
- Accountability
Architecture and AVG / GDPR
Levarne provides a secure architecture based on The General Data Protection Regulation (EU) 2016/679 (GDPR). "No individual user data is stored near the user's identity." The General Data Protection Regulation (GDPR) has seven design principles:
- Lawfulness, fairness and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality (security)
- Accountability