User identity management and Policies
Implementing user management functions to provide users with certain capabilities and manage their roles in the application. Login through social login or email login. Lost password flow, user data disconnected from the user. Log in with QR code, mobile in combination with desktop screens.
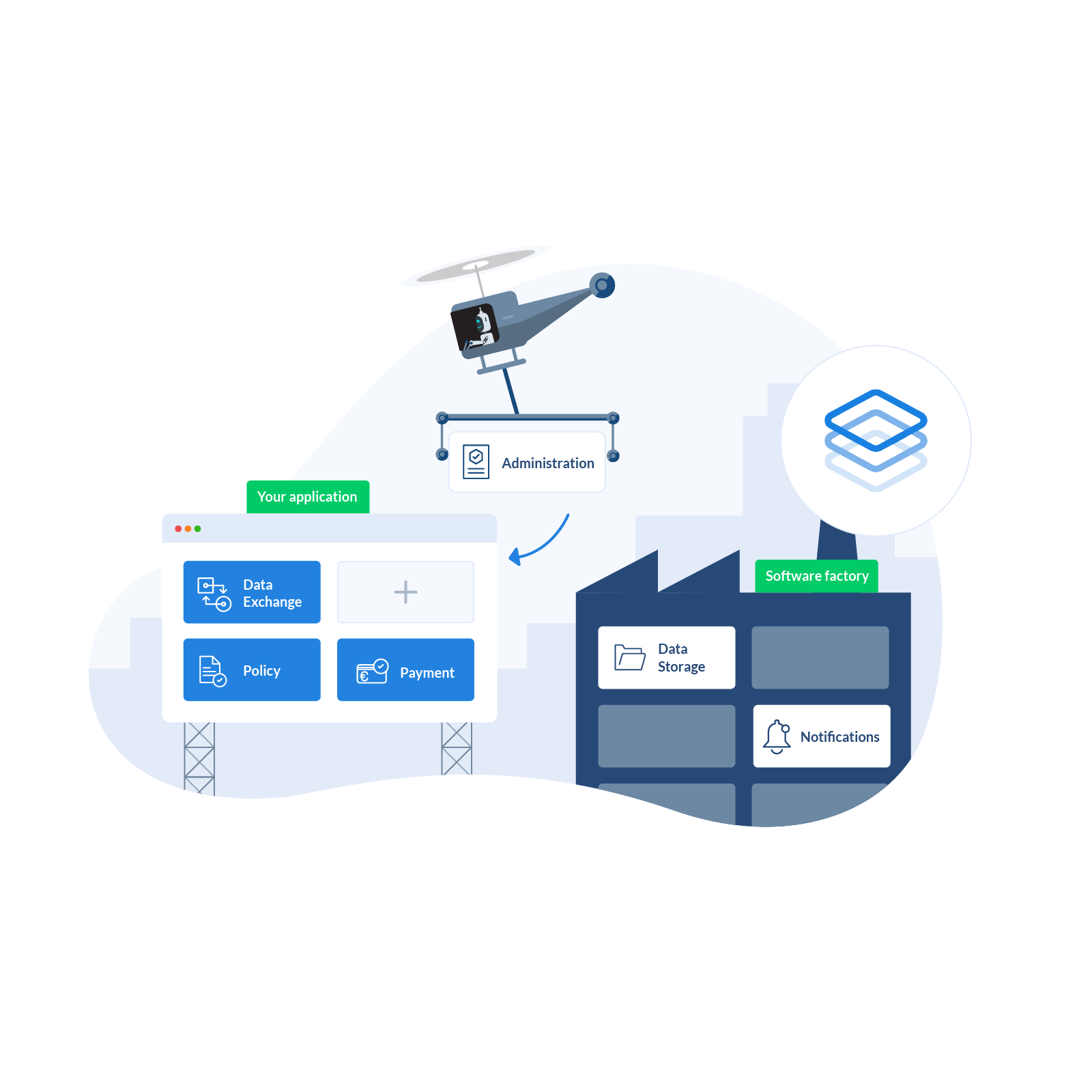
The policies apply to all applications that use the pool of users. So all policies also apply to all applications and application functions. By introducing an administration layer, again bound to the same mechanisms, users become simple processes to notify, create or modify.